Nujud Turki ALHajri
Saudi Arabia Military Industries AEC, Kingdom of Saudi Arabia
nujud.alhajri@gmail.com
Abstract #
This paper is intended to elaborate on the 4th Industrial Revolution (Industry 4.0) that will alter and shift technologies and the utilities sector. Alongside advanced Cybersecurity technologies to be aligned with the need for more resilience and secured environments that empower digital transformation. Where we explore the drivers and applications of Cybersecurity considering 4thIR as an engine of digital transformation, that is governed and measured by complying with digital transformation rules, flowing from modern technology to the evolution where the quality of life is measured by its speed, energy, and security. As such, Industrial Control Systems (ICS) are a solid infrastructure for such a digital transformation. As the acceleration of cyberattacks are becoming more sophisticated, a well Cybersecurity strategies must be applied. Furthermore, we propose advanced Cybersecurity solutions for the smart grid that can be addressed by the efficiency of the Next Generation (SOC) and the utilization of Distributed Ledger Technology (DLT).
Keywords – Cybersecurity, Digital Transformation, Energy, Fourth Industrial Revolution
1.Introduction #
As we live in the era of the 4th Industrial Revolution (IR), where a huge momentum and global trend of Energy and Digital Transformation in the utilities sector is represented in the Smart Grid and Smart Meter Projects; that are taking the headlines of mega projects worldwide as an application of Digital Transformation. With installing more than 600 million smart meters worldwide. Saudi Electricity Company, accomplished in record time the Smart Metering Project (SMP) as a model of Digital Transformation. Within a year’s time, 10 million smart meters, of which 4 million meters, equivalent to 40% of them were built in Saudi Arabia from locally manufactured components, were installed all over the Kingdom to provide customers with a smart digital experience, complying with digital transformation demands to improve the efficiency, reliability, and quality of services in the utility sectors.
Digital transformation is utilizing all forms of technology to digitalize business and lifestyle. However, it is not as simple as it seems when it comes to digitalization in utility sectors (ex. Electricity, Energy). It has a much broader meaning than just business transformation. Smart grids and meters are a tangible sample of projecting 4IR and its challenges in utilities to comply with digital transformation demands. An Industrial Control System (ICS) is a concept that combines a range of industrial control systems as in Supervisory Control and Data Acquisition (SCADA), and Distributed Control System (DCS) technologies that encompass many components and controllers in the environment, such as Intelligent Electronic Devices (IED), programmable logic controllers (PLC) and many others that are managed and configured to achieve an industrial objective execution.
It is quite challenging to anticipate cyber-attacks in different interconnected systems and infrastructures between IT and OT environments as in ICS when it comes to the utilities sector. Although each area is seen and managed separately, it is proven that all systems are interconnected and must be secured, controlled, and visible from all aspects to ensure a steady digital transformation. Fourth Industrial Revolution Systems are known to be hybrid and connected towards performing industrial executions and operations, Distributed Ledger Technology is a decentralized technology that is considered an enabler of such operations while providing security features and opportunities across the network, as well as resolving network security complexity, gaps and concerns as it will be highlighted in this paper how Decentralization is a recommended Cybersecurity solution for complex and critical infrastructure.
2.Digital Transformation in Utilities #
A concept that drives the 4th Industrial Revolution (IR) wheel to adjust and reshape all businesses and economics in utilities by underlying digitalized solutions to meet the 4IR vision and the world’s demands and needs; by enhancing quality of life in different aspects. This can be seen in enhancing fuel efficiency, uninterrupted daily operations, ensuring quick resolution of defects, maintenance activities, and higher productivity across all sectors. Digitalization in utilities forces an advanced understanding and implementation of smart grid communication, controls, automation, and innovative technologies aligned to form the mean of 4th IR towards providing a more reliable, greener, and most importantly secured grid.
Nowadays, there are opportunities and capabilities that have been handed to smart grids to ensure more sustainable, efficient, and smarter grids. Smart grid technologies when chosen and utilized as needed, it will ease the transition and the shift to a sustainable grid. A flexible and resilient strategy in implementing technologies that balances risk in utilities is a promising approach.
A. Utilities and Power Systems Evolution over the years
| 30 Years ago | Grid stability |
| 5 Years ago | Renewable integration |
| 3 Years ago | Demand response/DER(Distributed Energy Resources) |
| Today | Smart buildings and smart cities |
| Future | Next-GridAn open, flexible, interconnected model for energy
Flow-based markets, DER integration New distribution grid management/microgrids Further expansion of grid digitalization |
Table 1
SOURCE: Digital Utility Transformation Pwc Power & Utilities Roundtable Discussion Paper
B.Renewable Energy (RE) integration to Smart Grid
A stable source of energy is a global demand to power machines that run power generation, distribution, and other crucial functions of our life. The efforts continue toward increasing energy efficiency while reducing operational expenses. Accordingly, Vision 2030 programs have contributed to enhancing sustainability in RE and diversifying the government’s sources of income in the energy sector by developing non-oil revenues while reducing operational expenses (OPEX). In the same context, Renewable Energy (RE) serves the purpose of having power stability and can be referred to as the ultimate resource of stability and greenness of human beings. With its great impact that will be brought to the world by diversifying energy sources while reducing the dependence on imported fuel, as well as in producing economic development opportunities. It is a shared responsibility and a common interest toward sustainable, cost-effective energy solutions to the world. Such a transition will require upgrades of old grid systems and new innovative solutions to accommodate the different nature of renewable energy solutions.
The smart grid enables newer technologies to be integrated such as wind and solar energy production, further advances can be anticipated that will make the entire power grid smarter, as smart grids are able to incorporate such a transition. The simulation shown in Figure 1, simulates the role of Renewable Energy (RE) when integrated with smart grids.
C. Statistics and Numbers
Research stated that between the years (2018-2023) the utility industry will spend a total of $84 billion on building and implementing smart and digital infrastructure. The infrastructure of the utilities sector is being streamlined and renovated with a high investment, and more digital technology and connection between IT and OT environments, as in smart grids. This transition to “Smart Infrastructure” signifies a rapid shift in the utility sector. Case studies show that a transformation towards renewables is already happening, and several studies suggest that even higher shares of renewable energy power generation are foreseen.
The International Energy Agency’s (IEA) “sustainable future” scenario shows renewables providing 57% of world electricity by 2050.
Based on data record and Statistical Review of World Energy 2022, the below was found:
[1] The share of Renewable Energy in global power generation continued its rise, driven by strong expansion.
[2] Renewable Energy share has increased to almost 13% in 2021, higher than the increment share of Gas and Coal.
[3] The share of Coal increased slightly from 35% to 36% in 2021 and remained below its 2019 level.
[4] The share of Gas generation in 2021 remained close to its 10-year average level.
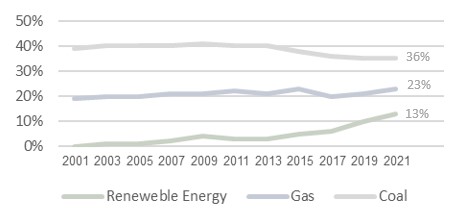
Fig. 1. Renewables in Global Power Generation
SOURCE: bp Statistical Review of World Energy
D. Smart Grid and Smart Meters
The concept of smart grid has been introduced as a new vision to shake off the traditional power grid to an efficient way of integrating advanced technologies and strategies. “We need to pool resources, connect assets, automate optimization, trade energy and empower consumers to adapt their behavior in line with the needs of the grid – ultimately, we must use digital solutions to ensure that each component and system works smarter, not harder.”, with these words gridX CoFounder, Andreas Booke summarized the perfect strategy to utilize smart grids.
The demand for reliable and efficient power generation, transmission, and distribution systems is an essential and vital demand. As traditional power grids are known to be centralized, The SCADA module in modern power systems collects data at remote terminals, transmits, and stores it in the main control center. This centralized data collection and storage is highly vulnerable to cyberattacks. With one-way limited communication, dialog makes it difficult for the grid to respond and interact with the instability and changes of energy. Smart grids have developed a different meaning of how power can be delivered and communicated in an efficient way that improves the reliability, security, and stability of the grid. As they are advancing towards the next-generation grid, with a two-way communication dialog that takes power systems to a higher level with decentralized networks and advanced control systems, that ensure resilience of power utility and enable flexibility. While decentralizing the operations and management of the smart grid has many benefits, it also brings security concerns; the more systems and environments are connected, the more Cybersecurity importance will rise.
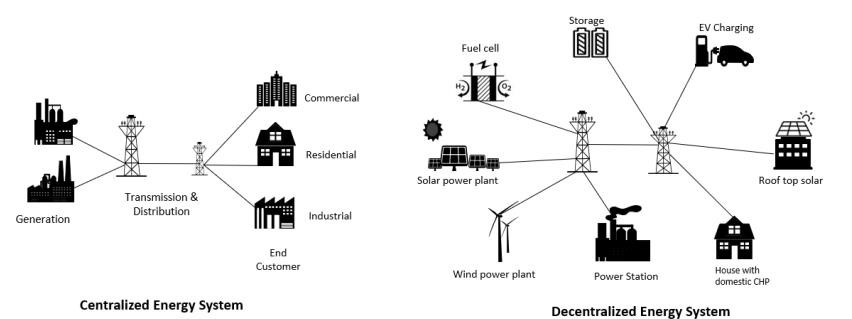
Fig. 2. Centralized vs. Decentralized Power Grid
3. Cybersecurity Consideration – Next Generation SOC Using SIEM and SOAR #
Both SIEM and SOAR collect log and event data from applications and network devices, but each solution operates differently when it comes to alerts or threats. Security Information and Event Management (SIEM) and Security Orchestration, Automation, and Response (SOAR) contain similar components and tools that empower the SOC environment, it might be hard to differentiate between them due to the similarities of the components. however, the distinction between them can be addressed in the core functionalities and capabilities, human intervention, and source of data. As illustrated in Figure 5, shows how SIEM orients events and will only provide the alert. For more investigation, SOAR will be used to automate the investigation path workflows which can significantly cut down the amount of time required to handle alerts.
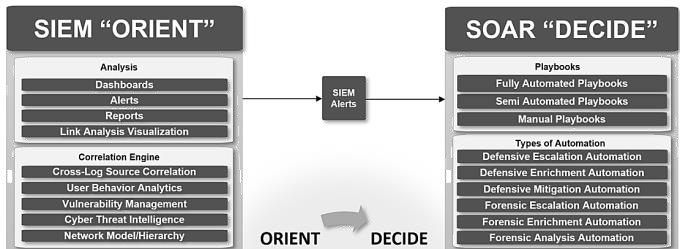
Fig. 3. SIEM “Orient” and SOAR “Decide”
A. SIEM
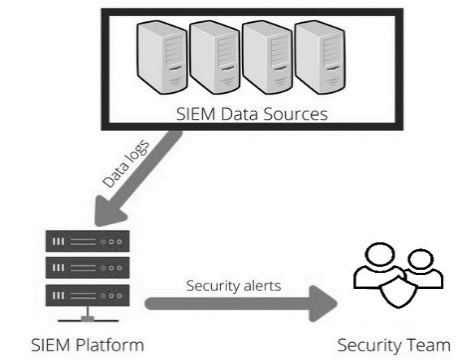
Fig. 4. How SIEM Works
SIEM is involved in the collection and correlation of security logs and data from the different log sources within the SIEM environment. The log sources in SIEM can be derived from servers, network devices, firewalls, IDS, and IPS. This correlation is achieved, and analysis is carried out of the logs either by the analyst monitoring the SIEM solution or automation is involved, and alerts will be raised from SIEM solution.
Firewalls, network appliances, and IDS systems generate a huge amount of data, which may exceed the capability of Cyber Security teams to handle or to be responsible for such an event. A SIEM makes sense of all the derived data by collecting, and aggregating, thus identifying, and analyzing incidents and events. This can be achieved using analytics software, and dedicated sensors.
B. SOAR
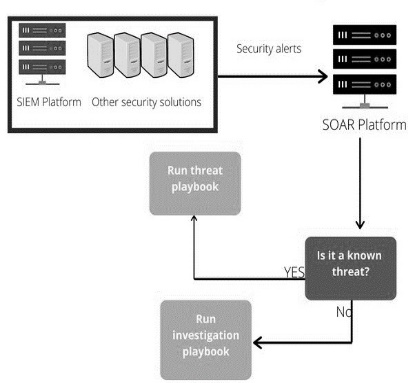
Fig. 5. How SOAR Works
SOAR is designed to help Cybersecurity teams to manage and have better visibility while responding to endless alarms. It’s known as a platform that takes SOC a step further by combining comprehensive data gathering, and analytics to provide the high management the needed visibility and ability that allow them to predict to implement sophisticated defense-in-depth capabilities based on what has been presented. SOAR combines advanced cyber technologies, as in:
- Security Orchestration and Automation (SOA)
- Security Incident Response Platforms (SIRPs)
- Threat Intelligence Platforms (TIPs)
These technologies are gathered into a product that allows IT and OT people to streamline security processes in three domains: threat and vulnerability management, incident response, and security operations automation that automate the handling of security operations tasks. As in executing these scanning for vulnerabilities or searching for logs without human intervention. Moreover, SOAR will pull information from external emerging threat intelligence feeds, endpoint security software, and other sources to get a better overall visibility of the security landscape inside the network.
4. Distributed Ledger Technologies (DLTs) Impose Many Cybersecurity Opportunities #
Distributed Ledger Technologies (DLTs) are technologies enabling parties with no trust in each other to exchange any type of digital data on a peer-to-peer basis with fewer intermediaries. It’s used to verify transactions, control deliveries, monitor workplace operations, and more. Blockchain is the most powerful and highlighted technology when it comes to the DLTs. It is known as a database (ledger) operating in a distributed manner in a network of multiple nodes or computers that keeps track of data transactions. A blockchain is run through a distributed network of participants who do not necessarily trust each other but follow the same rules (consensus).
A blockchain consists of blocks, ordered in a time-sequential manner, secured, using a hash function, as illustrated in Figure 8. The block is timely stamped and consists of transactions so it cannot be backdated, and it is immutable. A collection of data transmitted by each device node within the blockchain, and relevant details of the data are included, to ensure the traceability of the blockchain, each block will have its own timestamp (unique tag). The block is designed of two main parts:
- Block headers, where it link to the front blocks while providing integrity for the blockchain.
- The block body records the updated data information in each node.

Fig. 6. Blockchain Transaction Modal in ICS
A. Blockchain Transaction
When a transaction is initiated as illustrated in Figure 9, it is pooled in a block candidate (process no. 1), and nodes in the network validate the transaction (process no. 2). There will be many versions of block candidates since every node adds its address into the block candidate, but there must be only one block candidate added to the blockchain at a time. A consensus mechanism is then used, it is an automated process that ensures all participants accept or validate a block of identical copies of the distributed database files, and choose which block to be added (process no. 3).
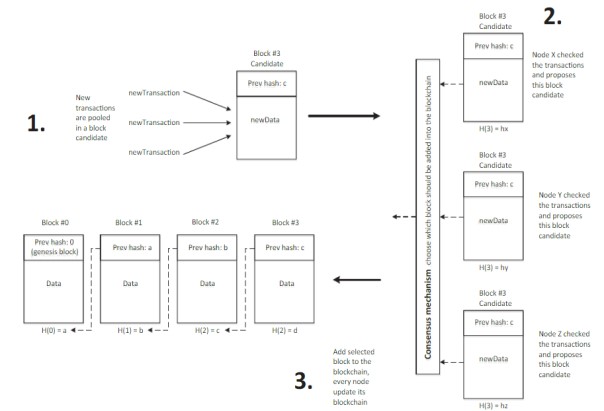
Fig. 7. Blockchain Transaction Scenario
The cycle is then repeated and once the data entered the blockchain, the data cannot be altered or modified. In this manner, a blockchain maintains the traceability of an asset and it is preferable for auditing.
B. Blockchain Applications in Smart Grid
Many researchers believe that Blockchain is the vital strategy and technology trend that will move the smart grids to the next higher level. Security, trust, and privacy of the system in an environment are mandatory considerations to have for any transaction of information in such environments.
The development of blockchain technology with its promising features will smooth the shift toward a decentralized and trusted approach that also provides a basis for smart grid evolution. Blockchain technology provides a desirable solution to smart grids which captured the interest of its adaptation. It can be implemented in different parts of the grid such as power generation, power transmission, and distribution.
C. Cybersecurity in Blockchain Technology
Blockchain is a decentralized approach, and this makes it a proper technology for Cybersecurity with its components and features as illustrated below.
| Network users | A user with a digital signature and two keys (public and private). |
| Nodes | Refer to devices on the peer-to-peer network that form a Blockchain infrastructure. |
| Transaction | Includes Public key of the receiver, data, and sender key. |
| Authentication | Nodes to authenticate transactions. |
| Blocks | Blocks that are created by validator nodes that select pending transactions to be added to the chain. |
| Blockchain | Validated blocks are linked to each other with a unique hash. |
Table 2
Main Components of a Blockchain In Cybersecurity
Smart Contract – Smart contracts are programs and digital contracts stored on a blockchain that are automatically executed when predetermined terms and conditions are met.
Transaction endorsement via consensus algorithms – the consensus algorithms enable to collectively report and block malicious users, nodes, and apps while ensuring reliability in a network involving multiple users or nodes.
Data integrity – Data in BC are designed as ledgers, every block is linked using cryptographic hash functions. Once a transaction is recorded on the blockchain, it can’t be changed, thus, any changes to the recorded data are processed as new transactions.
Availability – As each node in the network has a copy of the distributed ledger (shared database), the correct blockchain remains accessible to other nodes even in the case of a corrupted node.

Fig. 8. Blockchain (BC) in PP
D. Blockchain Application – BC Microgrid Accenture SAP Intelligent Solution
In today’s environment, decreasing investment costs of sustainable solutions and the acceptance of energy evolution are further pushing the transition from fossil fuels to renewables. This shift, however, makes it difficult for energy operators to balance supply and demand for home and business consumers. But with technological advancements and developments in the energy industry, new opportunities are present for consumers and operators to gain better insight on energy flows and more efficient energy usage. One such opportunity is a distributed landscape in which decentralized energy production is being consumed locally and surplus is delivered back to the grid and dozens of locations. This new model also allows consumers to become prosumers, allowing households and businesses to share and sell their excess energy. One step further and communities transform into connected microgrids, exchanging energy. Blockchain and DLT offers a practical view on optimizing a microgrid in an integrated scenario. Advanced EMS offers an enabling platform to facilitate local trading, enforces matches between demand and supply by smart contract on the blockchain, and integrates with SAP ERP application for invoicing and billing purposes. The blockchain solution framework allows immutability and transparency of the energy market and enforces the settlement of supply and demand orders through smart contracts.
The integration with SAP ERP demonstrates the connectivity potential for these new technologies. If fully implemented, here is how the solution will look in a microgrid:
- A prosumer produces energy locally; their household then consumes this energy while the surplus is automatically pushed as a sales order onto the marketplace.
- A community member with an energy shortage will push demand orders to the marketplace.
- The EMS forecasts demand and supply and the blockchain takes care of the matching and enforcing the contracts.
SAP ERP then provides the invoice and billing process, showing the microgrid balance and grid consumption and production. Consumers will benefit from the lower prices of the locally produced energy, while prosumers can generate cash on their sold surplus. Grid operators benefit from savings in both operational and capital spending. The result of combining the right technologies in the best right way will create in its turn a grid that is sustainable, efficient, and secure.
5. Recommendation #
Old principles do not convey with the new generation of intelligent Industry Revolution (IR 4.0) that relies heavily on automation and hyper-connectivity. The centralization and connectivity of power systems and grids represent weaknesses and concerns for the industry as they are becoming more complex. Moreover, the changing nature of the power grid and utility sectors, and the growing connectivity of the electricity ecosystem are bridging OT network in the Industrial Control Systems (ICS) with IT network introduces challenges to Cybersecurity teams. These challenges force a decentralized approach to be followed when it comes to ensuring a Cybersecurity approach and solution that empowers such a complex environment.
- Resources Allocation
A decentralized Cybersecurity approach consists of distributed resources and workforce for each location and site. The process of assigning and managing resources and assets in a way that assists Cybersecurity strategic planning goals while increasing the level of visibility. Moreover, Policies will be forced and aligned with each location’s specific model and needs and each site is managed and empowered by what it needs. Alongside the needed awareness and training for CS teams that each site might require. Where in a centralized approach, it requires all sites to agree on roles and policies that are to be used throughout a particular Cybersecurity scenario.
- Distributed Ledger
Distributed ledgers use independent device nodes to record, share, and synchronize transactions in their respective electronic ledgers. Instead of keeping data centralized as in a traditional ledger.
- Security, Trust, Performance, and Transparency
Decentralizing the processes of collecting and verifying data will add resilience to the grid and reduce the challenges of performance in a centralized grid. The approach to create security and trust with technologies is to assume that all participants are mutually untrusted, and trust is created by the consensus mechanism of the Blockchain. Transactions in a decentralized manner are encrypted, which makes them extremely secure. Each record is connected to the previous and subsequent records on a distributed ledger, all blocks will be chained via cryptography. This would strengthen the sense of security, and trust of the data as they are immutable while ensuring quite tight security. Moreover, A decentralized approach enables trust that improves communication between various nodes in a network, due to a shared view of transactions. Moving at the speed of trust is what can define a decentralized solution.
6. Conclusion #
The concept of the fourth Industrial Revolution promises prosperity and smart solutions for the utility sector. Challenges to smart infrastructure and smart grids will increase, and they can be overcome by utilizing leading technologies in a decentralized manner to optimize and automate the technologies in a scalable, efficient, and cyber-secure manner. Industrial infrastructures are known to be challenging in many perspectives. Therefore, it’s important to ensure the right technologies approach that drives and controls power generation, transmission, and distribution grounded by a steady Cybersecurity strategy as they are becoming more interconnected in IT and OT environments. Further, Confidence and trust in data and technologies that are used is a key advantage for society to gain from the potential opportunities that the Digital Transformation in line with the 4th Industrial Revolution can bring.
References #
[1] Blockchain Microgrid – Accenture SAP Intelligent Solution
[2] Digital utility transformation. (2015). PwC Power & Utilities Roundtable Discussion Paper, 1–16.
[3] “gridX – 10 Elements of Smart Grids That Will Enable Smart Cities.” gridX – 10 Elements of Smart Grids That Will Enable Smart Cities, Feb. 2022,www.gridx.ai/blog/10-key-elements-of-smart-grids-that-willenable-smart-cities.
[4] Kempener, R., Komor, P., & Hoke, A. (2013). (working paper). Smart Grids and Renewables.
[5] Mao, M., & Xiao, H. (2018). Blockchain-based Technology for Industrial Control System CyperSecurity. Advances in Intelligent Systems Research, 147.
[6] Musleh, A., Yao, G., & Muyeen, S. (2019). Blockchain Applications in Smart Grid – Review and Frameworks. IEEE Access, 2–8. https://doi.org/10.1109/ACCESS.2019.2920682
[7] Saudi Electricity Company – Smart Meters Project.
[https://www.se.com.sa/en-us/customers/Pages/SmartMeters.aspx]
[8] Stouffer, K., Pillitteri, V., Lightman, S., Abrams, M. and Hahn, A.(2015). Guide to Industrial Control Systems (ICS) Security. [online] National Institute of Standards and Technology(NIST). Available at: https://nvlpubs.nist.gov/nistpubs/specialpublications/nist.sp.800-82r2.pdf.
[9] Younasa, U., Khana, B., Alia, S., Kamalb, A., & Vaccaro, A. (2016). Cloud Computing Demand Response and Plug-in Electric Vehicles as Energy Management Tool for Smart Grid. Proposed Model Formulation.
[10] (2022). (rep.). bp Statistical Review of World Energy (71st ed., pp. 1– 60). London.







